How to Cheat at Managing Information Security

The development, appreciation, and expression of the security strategy and plan are the single most important factors in setting the security tone for an organization (see Figure 2.2). If you try to achieve a level of security that is too ambitious and inappropriate for the organization, you will not retain support from management. They will soon see that you are pumping money and head-count where it is not effective. Yet unless you take a high-level, whole organization approach, you will never obtain the backing or the funding to enforce any policy you write. The management will just not get it.
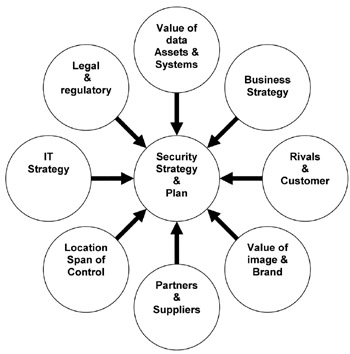
The strategic planning process for the whole enterprise, as we described it, considered several key factors. The security planning process should consider the same factors which is not surprising, since it is fundamentally the same process, only focused on information security. These factors are:
Legal and regulatory Health, government, and finance have specific legal and regulatory requirements for security. In the case of the government, these requirements are very specific. In the banking industry, the requirements may be more stringent but open to a level of interpretation. However, most industries have to consider such legalities as privacy, data protection, and human rights legislation. For more details, see the chapter on law later in this volume.
Business strategy If the CEO is determined to brand the organization as the
